-
Notifications
You must be signed in to change notification settings - Fork 15k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Unable to frame site whose CSP contains frame-ancestors * inside <iframe> or <webview>
#26369
Comments
|
does this also occur in Chrome? |
|
@nornagon, nope, Chrome displays it without trouble, and so does Edge: |
This PR essentially reverses #2797. Currently this doesn't work because the `frame-ancestors *` directive prevents VS Code from framing TensorBoard. This is because VS Code is an Electron application, and Electron appears to be unable to frame websites which set `frame-ancestors *` in its response headers: electron/electron#26369 If I'm reading the CSP specification correctly, omitting the frame-ancestors directive altogether is equivalent to setting `frame-ancestors *`, so to my knowledge this PR should not result in a behavior change for environments which correctly implement the CSP spec. From https://w3c.github.io/webappsec-csp/2/#directive-frame-ancestors: > The term allowed frame ancestors refers to the result of parsing the frame-ancestors directive’s value as a source list. If a frame-ancestors directive is not explicitly included in the policy, then allowed frame ancestors is "*".
|
@joyceerhl it looks like in Chrome you're hosting the iframe in the same origin as the child, whereas in Electron you're hosting it from a BTW, I made a version of your repro case using Node.js's |
This PR essentially reverses #2797. Currently this doesn't work because the `frame-ancestors *` directive prevents VS Code from framing TensorBoard. This is because VS Code is an Electron application, and Electron appears to be unable to frame websites which set `frame-ancestors *` in its response headers: electron/electron#26369 If I'm reading the CSP specification correctly, omitting the frame-ancestors directive altogether is equivalent to setting `frame-ancestors *`, so to my knowledge this PR should not result in a behavior change for environments which correctly implement the CSP spec. From https://w3c.github.io/webappsec-csp/2/#directive-frame-ancestors: > The term allowed frame ancestors refers to the result of parsing the frame-ancestors directive’s value as a source list. If a frame-ancestors directive is not explicitly included in the policy, then allowed frame ancestors is "*".
Backport of #4332 to 2.4. Cf. #4547. --- This PR essentially reverses #2797. Currently this doesn't work because the `frame-ancestors *` directive prevents VS Code from framing TensorBoard. This is because VS Code is an Electron application, and Electron appears to be unable to frame websites which set `frame-ancestors *` in its response headers: electron/electron#26369 If I'm reading the CSP specification correctly, omitting the frame-ancestors directive altogether is equivalent to setting `frame-ancestors *`, so to my knowledge this PR should not result in a behavior change for environments which correctly implement the CSP spec. From https://w3c.github.io/webappsec-csp/2/#directive-frame-ancestors: > The term allowed frame ancestors refers to the result of parsing the frame-ancestors directive’s value as a source list. If a frame-ancestors directive is not explicitly included in the policy, then allowed frame ancestors is "*". Co-authored-by: Joyce Er <joyceerhuiling@gmail.com>
|
I have the same issue. What would be the right solution for this? |
|
You can set an Here I simply remove all of them: win.webContents.session.webRequest.onHeadersReceived({ urls: [ "*://*/*" ] }, (d, c) => {
if (d.responseHeaders['Content-Security-Policy']) {
delete d.responseHeaders['Content-Security-Policy'];
} else if (d.responseHeaders['content-security-policy']) {
delete d.responseHeaders['content-security-policy'];
}
c({cancel: false, responseHeaders: d.responseHeaders});
}); |

Preflight Checklist
Issue Details
Expected Behavior
According to the content security policy specification, Electron should be able to frame a website whose response headers contain the
frame-ancestors *CSP directive by setting its URL as the source of an<iframe>or a<webview>. From https://w3c.github.io/webappsec-csp/2/#match-source-expression, at minimum http URLs should be treated as a match, not a violation, for a CSP directive whose source list is *:Actual Behavior
Electron reports a CSP violation for
<iframe>s or<webview>s whose source URL points to a website which sets theframe-ancestors *directive in its response headers.To Reproduce
Start a simple web server which sets the
frame-ancestors *CSP directive in its response headers. For example, to do this with Python:python -m pip install flaskapp.pypython -m flask runto startapp.pyelectron-quick-startsubdirectory. This is identical to https://github.com/electron/electron-quick-start, except that index.html contains an<iframe>whose source is localhost:5000:npm installand thennpm startto launch the Electron appIf you comment out the line that sets the CSP in
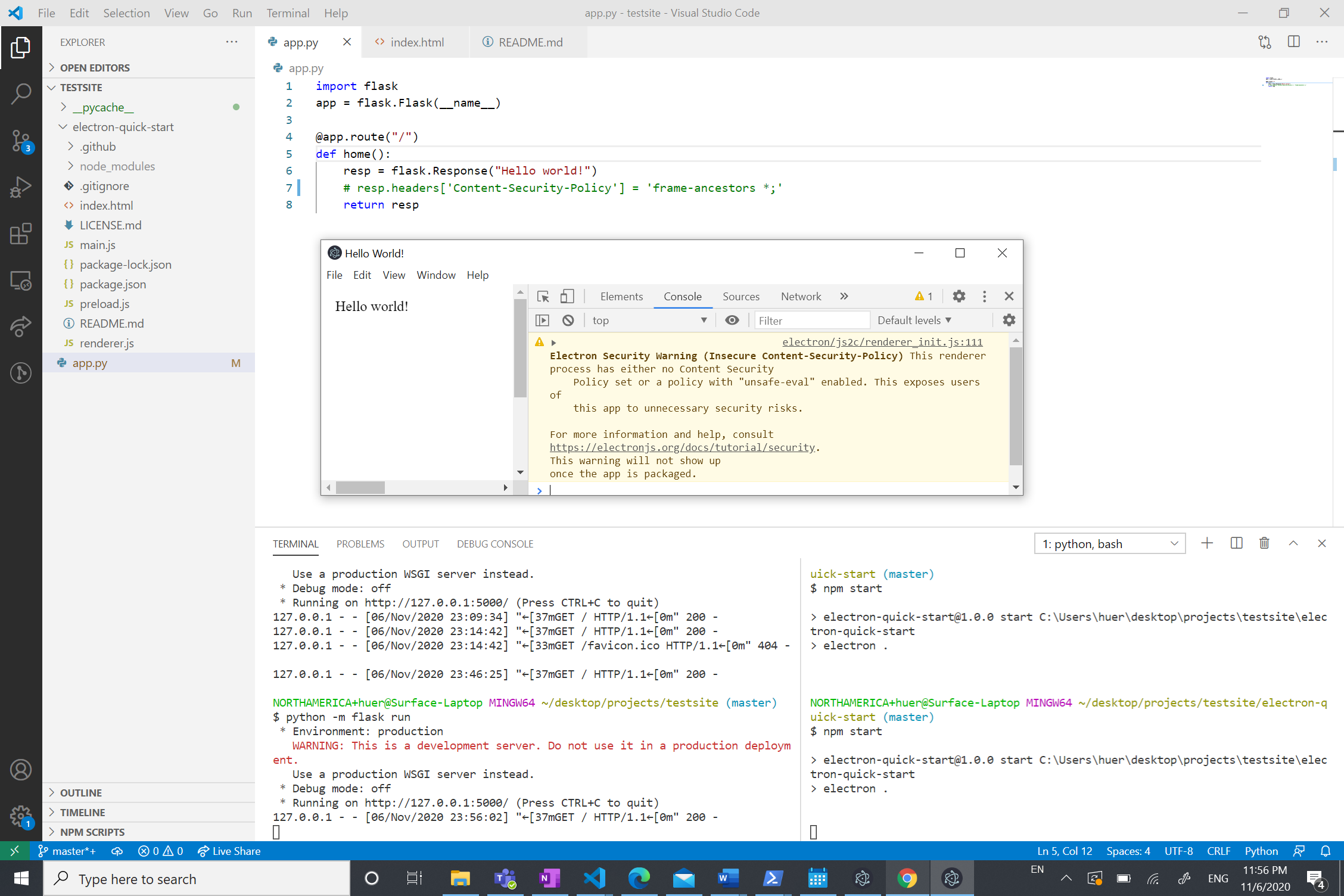
app.pyand restart the server, Electron has no trouble framing the website:This seems odd as
frame-ancestors *should be equivalent to omitting theframe-ancestorsdirective altogether. From https://w3c.github.io/webappsec-csp/2/#directive-frame-ancestors:Additional Information
I don't have control over the source code for the website that I'm framing (the broader context for this investigation is that I'm trying to frame the Tensorboard webapp, which is started and served locally, in an Electron environment), or I'd simply remove the
frame-ancestors *directive as a workaround. I'm filing this bug on Electron because Chromium-based browsers don't seem to exhibit this behavior, so this seemed like the right spot, but please let me know if I should file this elsewhere. Thanks so much for your help! 😊The text was updated successfully, but these errors were encountered: