New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
sops frozen while decrypting and consumes a full CPU #665
Comments
|
For information, I switch to a simple version of gpg tooling, without the GPGSuite (following installation guide from https://dev.to/wes/how2-using-gpg-on-macos-without-gpgtools-428f) The behavior is the same... I've set the I've add a line break to separate logs from each execution If I run a I've add a line break to separate logs from each execution This has been made with following versions of software: |
|
Sorry it took so long to respond, I missed this originally. That does not look right. Since it looks like it's SOPS that's stuck at 100% CPU, could you run it under a debugger or a profiler and see what's using that much CPU? I've never seen this happen myself, so no idea how to reproduce it. Maybe even a simple profile with Instruments would work, since you're on macOS. See https://help.apple.com/instruments/mac/current/#/dev147557f7 for launching instruments, then select Time Profiler and on the top left, where it says All Processes, narrow it down to only sops. Record a sample and share it here. Any other profiler works for me as well. |
|
To be sure, I need to install Xcode (the heavy one) or I can install just part of it to do that? |
|
I think you need the full Xcode. Alternatively, you could use pprof: https://golang.org/pkg/runtime/pprof/. Xcode is probably easier, except for the download times. |
|
I've followed the solution with Xcode: |
|
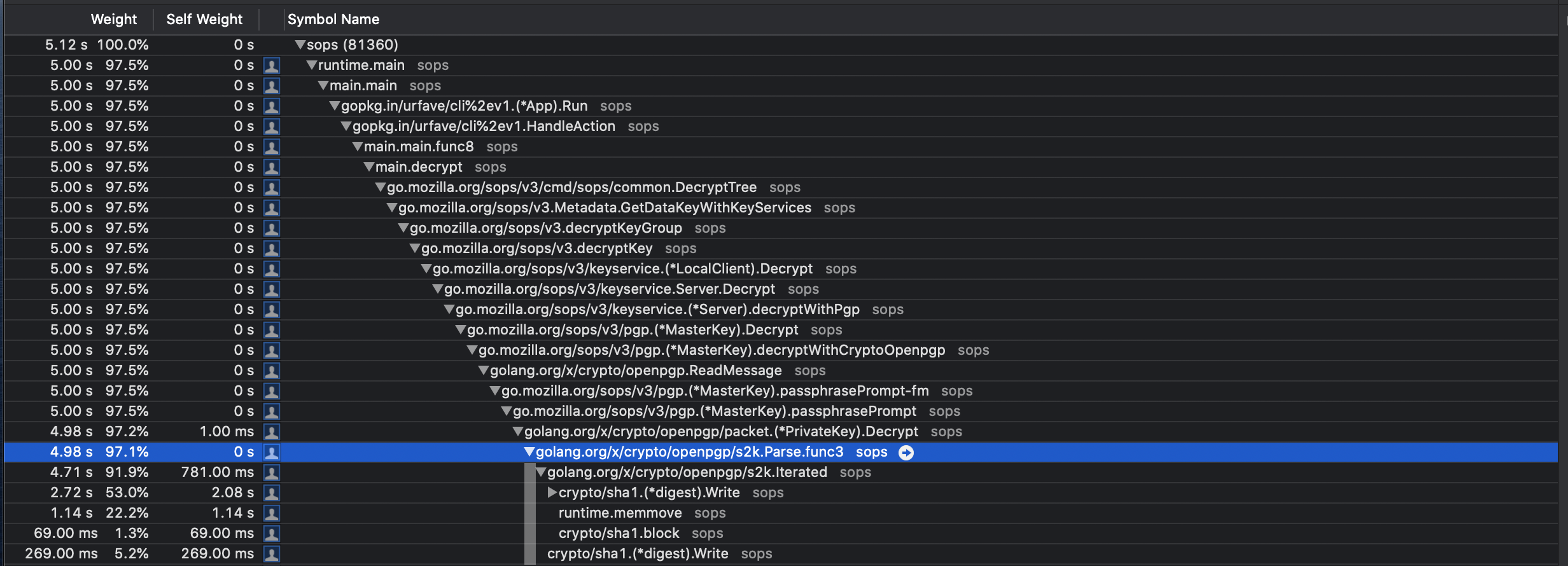
Interesting. All the time seems to be spent repeatedly trying to decypt the private key: Based on https://godoc.org/golang.org/x/crypto/openpgp#PromptFunction:
Our prompt function is here: And it calls Decrypt on the private key, so that seems like the possible culprit for 100% CPU usage. I'm not sure why the key would fail to unlock from the second time onwards, though. We could fix the 100% CPU usage issue by only allowing the prompt function to be called once, but that won't fix the other issue. |
|
You are talking about the In my case, I have a |
|
It should be the one in 350, yeah (unless you're being prompted for your passphrase, which you're not). I'm guessing decrypting with the Somewhat unrelatedly, I doubt the Go PGP implementation is used successfully most of the time. Maybe we should change the default to the GPG binary. |
|
I just stumbling upon this issue and I think it's related to #338 and a known issue in What's about tackling this issue by throwing an error in https://github.com/mozilla/sops/blob/4bc27f6eb72b1b4090753e9f3dba1d094544e1c3/pgp/keysource.go#L321 when it's called twice. Should this not address that problem? BR Uwe |
|
Hi @autrilla |
|
Maybe not limit it to once, to give people a chance to retry in case they input the wrong passphrase. But yes, limiting the number of attempts sounds good. I would be happy to review a PR for this :) |
This fixes getsops#665 See also golang/go#28786 In some strange situations it can happen, that openpgp.ReadMessage() runs into a endless loop. This seems to be triggered by a slightly inconsistency in key settings. It happened to me, but I wasn't able to reproduce it with a fresh key. A proposed solution from the x/crypto community was, to break this loop in the callback passphrasePrompt.
* Fix tests * Fix endless loop in x/crypto/openpgp func ReadMessage This fixes getsops#665 See also golang/go#28786 In some strange situations it can happen, that openpgp.ReadMessage() runs into a endless loop. This seems to be triggered by a slightly inconsistency in key settings. It happened to me, but I wasn't able to reproduce it with a fresh key. A proposed solution from the x/crypto community was, to break this loop in the callback passphrasePrompt. * Revert "Fix tests" This reverts commit 285f4dc. * Improve error description getsops#690 (comment)
Hi,
My problem is when I try to decrypt a file (env file for example), the first time the result is correctly shown, but if I run it
another time, the process will be stuck and will consume a full CPU.
I need to kill the
gpg-agentprocess to be able to "run again" the command, but like before, only once. The second execution will be stuck and the process will consume one CPU again.For information:
I've updated GPGSuite and sops to the last version to check if this could fix the bug... but without success
The text was updated successfully, but these errors were encountered: