New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Error: unknown option "staged" when running pre-commit with docker_image language #1022
Comments
|
I'm having the same issue. If I update things to remove the --staged flag from the gitleaks protect invocation and ask pre-commit to give me verbose output, it looks like git does not see /src as a git repo. However, if I mount the repo the same way as pre-commit is (or at least I believe the same way...) and exec into the container to run the same gitleaks command, it appears to work? |
|
I've encountered this as well. I believe the issue is due to pre-commit setting the That results in pre-commit running: Which results in the following: To fix, I changed my pre-commit config to be: Happy to help resolve if someone has a good suggested fix? |
|
We've encountered this issue in our repositories as well. The issue doesn't occur while using Orbstack for Mac. |
Describe the bug
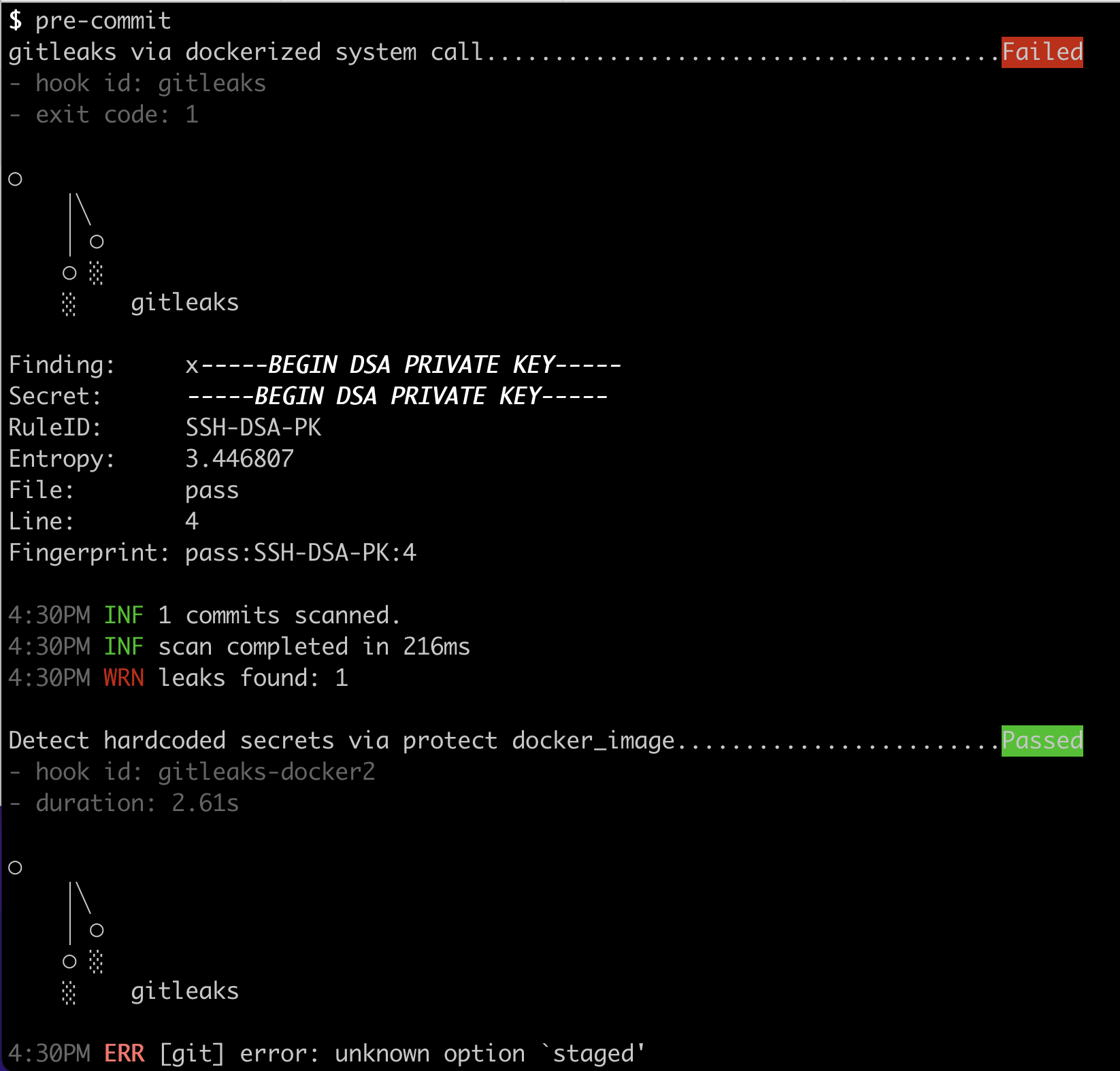
I'm seeing the unsafe directory bug
but I'm using the most recent container
zricethezav/gitleaks:v8.15.0
344cf751f79b 7 days ago 36.1MB
To Reproduce
Use the .pre-commit-config.yaml as suggested here
echo '-----BEGIN RSA PRIVATE KEY-----' > dirty
git add .
pre-commit
Expected behavior
The hook should run the same when using "language" docker_image as when run using golang (or system).
Screenshots
Basic Info (please complete the following information):
Additional context
The above output comes when I have the following .pre-commit-config.yaml
The "system" call is made using a docker wrapper installed to /usr/local/bin/gitleaks
Oddly, using "system" and calling the same command I don't see the --staged problem.
I'm wondering if the -v path might not be mounting correctly, but looking at the source code for docker_image.py it
seems to be calling the docker_cmd which does mount PWD to /src.
cc @zricethezav
The text was updated successfully, but these errors were encountered: