-
-
Notifications
You must be signed in to change notification settings - Fork 90
GraphQL authorization #419
Comments
|
Hi, On my APIs a use JWT then I add an User or a GuestUser to the GraphQL context then on each resolver I see in if there is a User the Context and if the User has proper roles. |
|
So your solution is conceptually the same as mine. Repeating permission checking on each resolver doesn't sound good for me, that's why I mentioned GraphQLite solution.
I don't know the source code of Siler good enough, but I would create new server directive $user = $context['user'] ?? \Siler\Container\get('user'); // or any other way to get current user...
foreach ($authorization->getConditions() as $condition) {
if (!$condition::check($user, $args)) {
throw new SomeSuitableException($authorization->getMessage(), ..., $authorization->getSomething());
}
} |
|
So, following the GraphQL's website recommendations:
Auth shouldn't be on any part of GraphQL solution, it should be in your business rules/domain layer. Anyway what do think about the Middleware pattern? Then you can define a pipeline and add it to run before reaching the resolver. |
|
Inside standard middleware I have no direct access to |
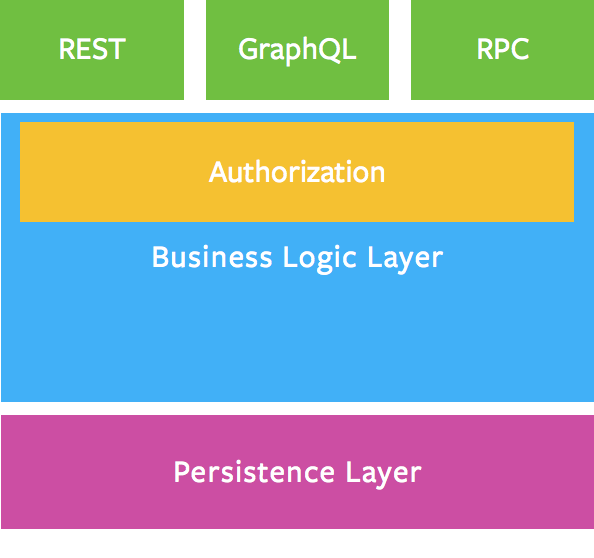
Hello,
What is recommended way to add authorization logic to Siler\GraphQL module? I'm aware of that authentication could be successfully done via route middleware, but the same cannot be done with authorization (or shouldn't... to achieve it anyway, you would have to parse request once more and fetch operation type, operation name and arguments recursively...).
For instance, package
thecodingmachine/graphqliteoffers@Securityannotations that are handled by authentication and authorization services that you set in schema factory.Are there any plans to implement similar feature to Siler\GraphQL? Or maybe solution already exists and I didn't manage to find it in documentation and source code? Maybe with dispatcher...?
I created actually a temporary workaround for this in Query class, but I wouldn't recommend it to anyone...
The text was updated successfully, but these errors were encountered: