New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Auth problem with private Docker registry when building from Dockerfile #389
Comments
|
After some research I found that Line 601 in 9dc7dbd
AuthConfig key.
I cloned the repository ands when I added below code it stared working as expected. buildOptions := types.ImageBuildOptions{
BuildArgs: img.GetBuildArgs(),
Dockerfile: img.GetDockerfile(),
Context: buildContext,
Tags: []string{repoTag},
AuthConfigs: map[string]types.AuthConfig{
"my.domain.dev:5000": {
Username: "user",
Password: "pass",
},
},
}Unfortunately currently there is noway to pass it from my tests. The |
|
Hey @rzajac thanks for opening this issue, it seems we are missing those credentials when pulling the building the image. I wonder if we are missing AuthConfig elsewhere 🤔
Sorry but I do not get this. Do you mean that you cannot test it because you'll be forced to expose your credentials in the code? If that's the case, have you tried to force a docker login in your build pipeline first? |
|
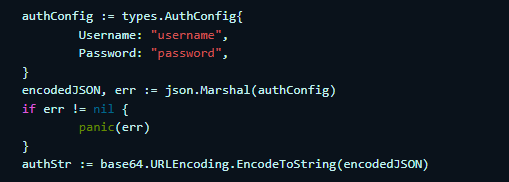
@mdelapenya I meant that with current way Since yesterday I found a workaround for this problem by pulling the image using Docker API before I use testcontainers. My function looks like below in case someone wants to know how i did the workaround: // PullImage uses Docker client to pull the image reference.
func PullImage(ctx context.Context, ref string) error {
cli, err := client.NewClientWithOpts(
client.FromEnv,
client.WithAPIVersionNegotiation(),
)
if err != nil {
return err
}
cred, err := RegistryCred(ref, "")
if err != nil {
return err
}
options := types.ImagePullOptions{
All: true,
RegistryAuth: cred,
}
rc, err := cli.ImagePull(ctx, ref, options)
if err != nil {
return err
}
defer func() { _ = rc.Close() }()
if _, err = io.ReadAll(rc); err != nil {
return err
}
return nil
}
// RegistryCred returns private registry credentials string for image. The dir
// should be path to the directory with Docker configuration file or empty
// string. The default config (~/.docker/config.json) will be used if the dir
// is set to empty string.
func RegistryCred(image, dir string) (string, error) {
cf, err := config.Load(dir)
if err != nil {
return "", err
}
named, err := reference.ParseNormalizedNamed(image)
if err != nil {
return "", err
}
domain := reference.Domain(named)
if domain == "docker.io" {
return "", nil
}
ac, err := cf.GetAuthConfig(domain)
if err != nil {
return "", err
}
encodedJSON, err := json.Marshal(ac)
if err != nil {
return "", fmt.Errorf("error when encoding auth: %w", err)
}
return base64.URLEncoding.EncodeToString(encodedJSON), nil
} |
|
I am getting the same error in pipeline "no basic auth credentials". We have uploaded images to AWS ECR and trying to pull images from there. The thing is we are doing docker login in pipeline before running these tests and still getting this error. |
|
I was facing the same problem. But when I looked into docker go pkg. I found how we can give the registry credential for auth docker pull. https://docs.docker.com/engine/api/sdk/examples/#pull-an-image-with-authentication So I gave the above auth str with my encoded registry credentials to RegistryCred as below in ContainerRequest. This worked from in my local as well CI pipeline. |
@rzajac could you please check with @mehulgohil's approach? If this is working for you too, I think we could close this issue |
|
@mdelapenya the above may work for static creds, but the docker build fails for me where I am using a credential helper to inject the credentials as ENV variables. This is far safer and the recommended approach |
|
@mdelapenya running into a similar issue on simple pull images from ECR (despite being logged in already). Looks like the go implementation for testcontainer does not handle loading the docker config.json when no RegistryCred are passed. The java implementation for testcontainer seems to handle this by default (https://github.com/testcontainers/testcontainers-java/blob/de1324ed2800eff4da326d0c23d281399d006bc0/core/src/main/java/org/testcontainers/utility/RegistryAuthLocator.java). Are you open for a contribution to implement a similar behavior in the go implementation? |
|
@rvichery thanks for pinging us about this issue, your contributions are super welcomed!! So feel free to elaborate a PR describing the use case it solves. Having Java code as a reference is a good thing to follow, so please reference it whenever you need it. |
@matdehaast sorry for the radio silence, for some reason this message felt out of my radar, my bad 😞 I know @rvichery is willing to contribute a fix, but if you want to participate too, I wonder if you both would be interested in opening a discussion to collaborate in the fix. wdyt? |
|
@mehulgohil nice work around, however, I am using multi-stage docker file with multiple private repositories so another problem is which credential to use at build time... I added this issue #532 to hopefully support multiple registry creds (@rzajac Can you please check if it make sense?) |
|
I think this issue can be closed, as #602 was already merged. Thank you all for creating such a healthy discussion 👏 |
Describe the bug
When building image from Dockerfile using private Docker repo I get en error:
Docker info
output of the command:
Additional context
docker pull my.domain.dev:5000/ifp-docker/dki-proftpd:v0.2.1and then i do not have this problem anymore.FROM dki-proftpd:v0.2.1 as source).The text was updated successfully, but these errors were encountered: