-
-
Notifications
You must be signed in to change notification settings - Fork 1.2k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
prevent CVE-2019-9740 in 1.24.x #1591
Conversation
|
I missed a few things on the fast-forward it looks like. Namely |
344a372 to
dd6d500
Compare
|
@sethmlarson just rebased |
|
Can you update the dotted_fqdn test the same way as it's update in master? ie skip it on GCE |
Codecov Report
@@ Coverage Diff @@
## 1.24-series #1591 +/- ##
===============================================
+ Coverage 98.74% 98.74% +<.01%
===============================================
Files 22 22
Lines 1826 1828 +2
===============================================
+ Hits 1803 1805 +2
Misses 23 23
Continue to review full report at Codecov.
|
a2e5ae6 to
83b5d5e
Compare
|
@sethmlarson do you know what's up w/ the How would you like me to proceed with that? |
|
Might have to apply this commit to the branch as well: d0255e0 |
83b5d5e to
c5351ec
Compare
|
@sethmlarson looks like Travis is still unhappy :/ Looks related to tests run on OSX? I might need some help making the |
src/urllib3/util/url.py
Outdated
| # Prevent CVE-2019-9740. | ||
| # adapted from https://github.com/python/cpython/pull/12755 | ||
| if _contains_disallowed_url_pchar_re.search(url): | ||
| raise LocationParseError("URL can't contain control characters. {}".format(url)) |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I recommend using a repr of the URL rather than the raw url containing the offending text in the error message. {!r} iirc.
|
Good point @gpshead, addressed. Here's with the latest version of this PR: >>> urllib3.PoolManager().request('GET', 'http://localhost:8000/ HTTP/1.1\r\nHEADER: INJECTED\r\nIgnore:')
Traceback (most recent call last):
File "<stdin>", line 1, in <module>
File "/home/ryanpetrello/dev/urllib3/src/urllib3/request.py", line 68, in request
**urlopen_kw)
File "/home/ryanpetrello/dev/urllib3/src/urllib3/request.py", line 89, in request_encode_url
return self.urlopen(method, url, **extra_kw)
File "/home/ryanpetrello/dev/urllib3/src/urllib3/poolmanager.py", line 312, in urlopen
u = parse_url(url)
File "/home/ryanpetrello/dev/urllib3/src/urllib3/util/url.py", line 164, in parse_url
raise LocationParseError("URL can't contain control characters. {!r}".format(url))
urllib3.exceptions.LocationParseError: Failed to parse: URL can't contain control characters. 'http://localhost:8000/ HTTP/1.1\r\nHEADER: INJECTED\r\nIgnore:' |
c5351ec to
25b856b
Compare
|
@sethmlarson I think I've got the correct things ported from |
|
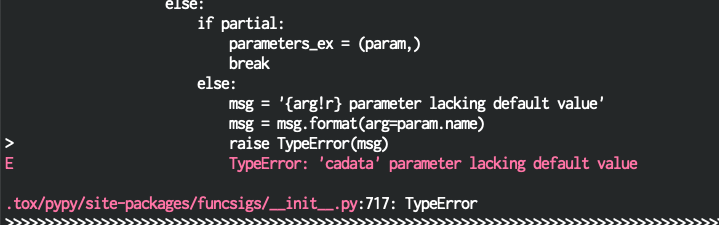
@sethmlarson pypy on 27 is failing for me, but it's also failing on recent commits to Might be a simple fix, but it seems outside of the scope of this PR: |
|
Thanks for the quick turn around on this 😄. At the risk of being a nag, what are the odds this will wind up in an official release on PyPI (1.24.3?) soon-ish? |


adapted from python/cpython#12755
related: #1553