The motivation behind this project is to create an open-source example for how to use the pac4j-kerberos library with the Spark Java Framework (not to be confused with Apache Spark), and then strengthening the security by adding HTTPS-encryption to all routes.
The project requires that you either have Docker installed or Java JDK 8 and Maven installed, and Postman is recommended for the testing.
The Spark Java documentation provides good documentations for how to set up HTTPS over SSL/TLS: http://sparkjava.com/documentation#embedded-web-server. It also references to the Oracle pages for how to create a KeyStore: https://docs.oracle.com/cd/E19509-01/820-3503/ggfen/index.html.
In this project, the following has been done to achieve HTTPS encryption over SSL/TLS:
- The
deploydirectory was created within./code/deploy. - The
keytoolwas used to generate a new KeyStore:keytool -genkey -keyalg RSA -alias keystore -keystore keystore.jks -validity 365 -keysize 2048
> At the password prompt, the password was set tosecretkey.
> For the "What is your first and last name?" prompt, enter the domain of the project. Since this is a local test project, just addlocalhost.
> Remaining fields should be filled out as you please and end it withyesat the last prompt if everything is correct. - The new
keystore.jkscan now be found at.code/deploy/keystore.jks. - The routes are then secured by adding
secure("deploy/keystore.jks", "secretkey", null, null);to theMain.java. It is important to add this before any routes are defined.
All pages will now require https:// to be used.
You will still get a warning about there not being a secure connection, since the certificate is not signed by a trusted entity (CA). Further details describing this process can be found here: https://support.code42.com/Administrator/6/Configuring/Install_a_CA-signed_SSL_certificate_for_HTTPS_console_access.
| HTTP | HTTPS |
|---|---|
 |
 |
The implementation of Kerberos authentication with pac4j requires that the dependency pac4j-kerberos is installed. mockito-core is used in this case for sandbox testing purposes.
The functionality implemented into this project was derived by combining the KerberosClientTests.java file and the spark-pac4j-demo project. It can be studied in further detail under the authorization directory.
In order to successfully authenticate with Kerberos, the header needs to have an Authorization key-value pair defined as follows: { "Authorization": "Negotiate <KERBEROS TICKET>" }
For this example, any base64-value for a KERBEROS TICKET will result in successful authentication.
| Unauthorized | Authorized |
|---|---|
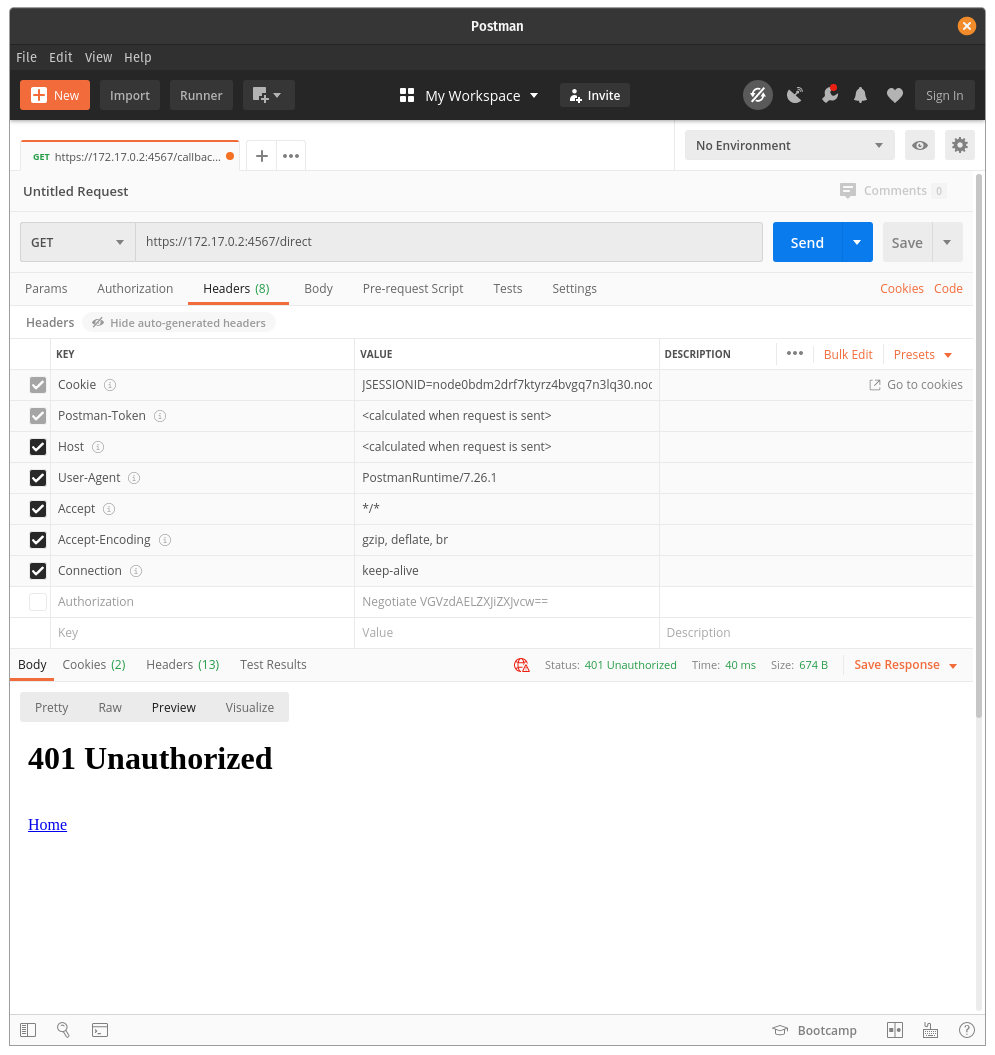 |
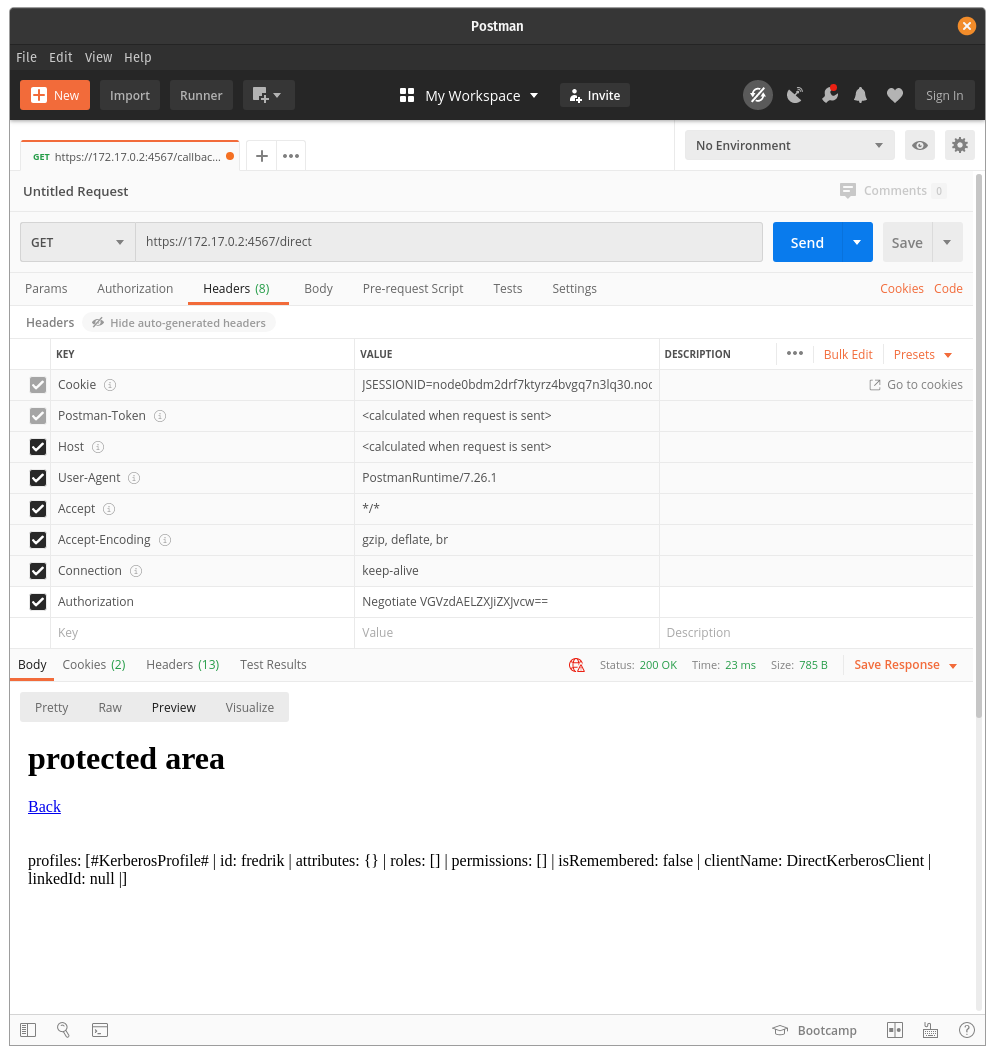 |
| Unauthorized | Authorized |
|---|---|
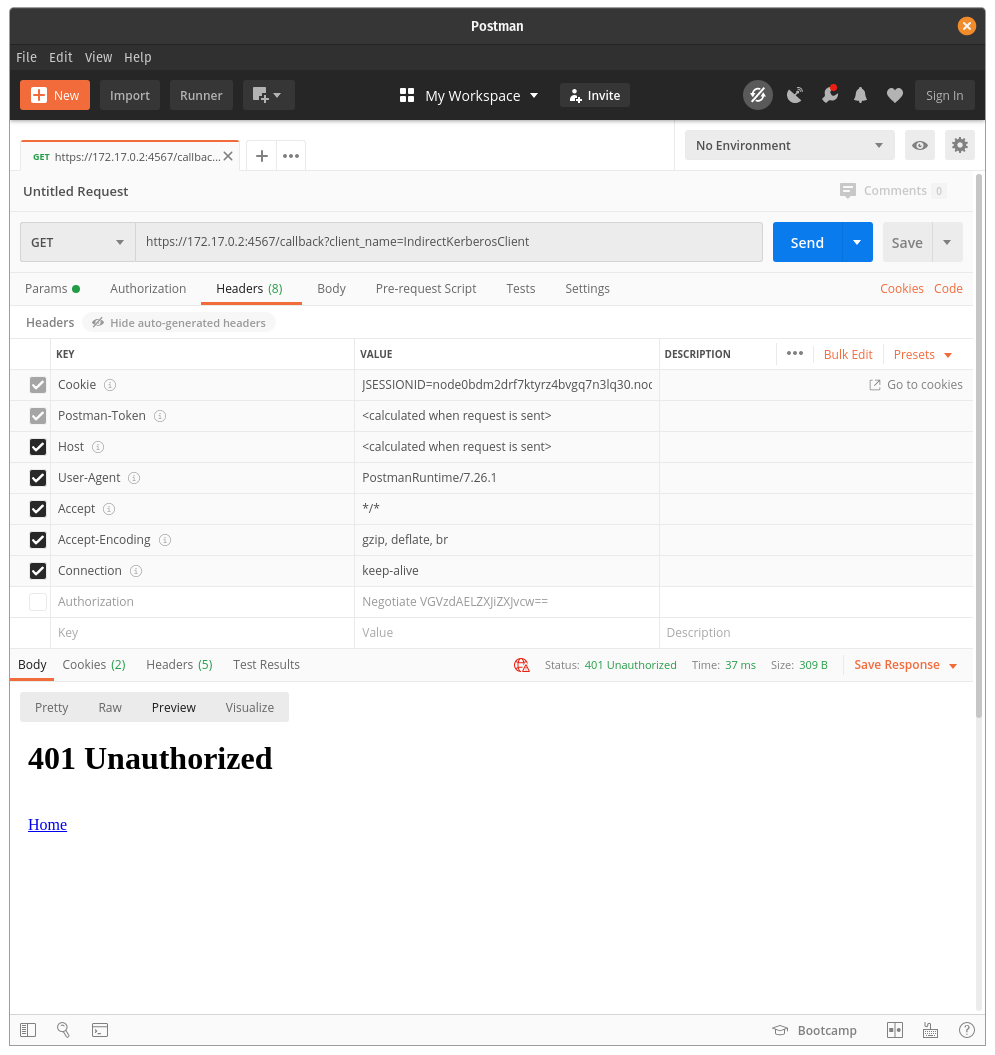 |
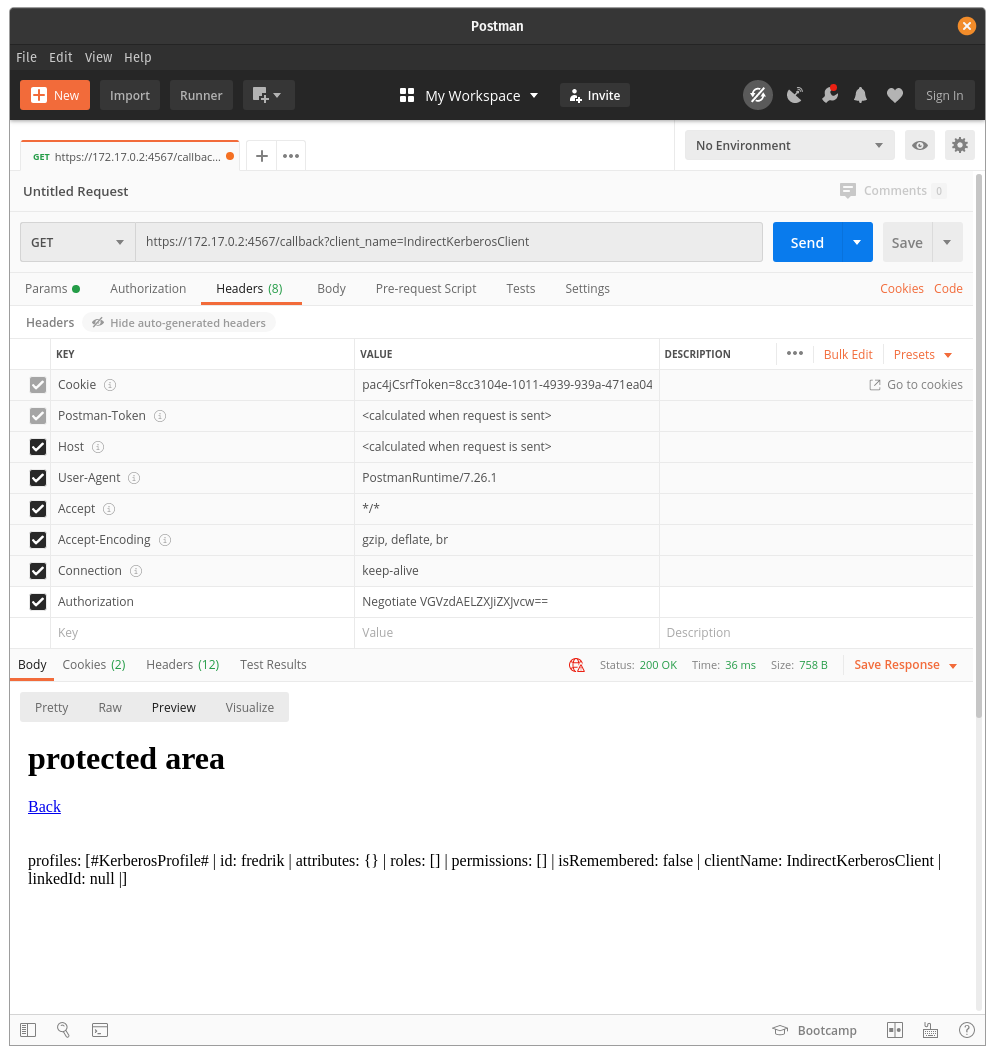 |
The current example is just a simple and local sandbox test, without any connection to a running key distribution center (KDC) with validation towards a Kerberos principal and keytab file. In order to implement this functionality, the ConfigurationFactory.java (lines 32-42) has to be updated to use the SunJaasKerberosTicketValidator, as described in the pac4j Kerberos documentation.