Offset x Offset sharp is the C# version of the program (offset x offset) that I have written in assembly around 2011 Its purpose is to find the viral signature of your programs i.e which part of the program is rising the flag, so you can change your program to avoid fake AV detections.
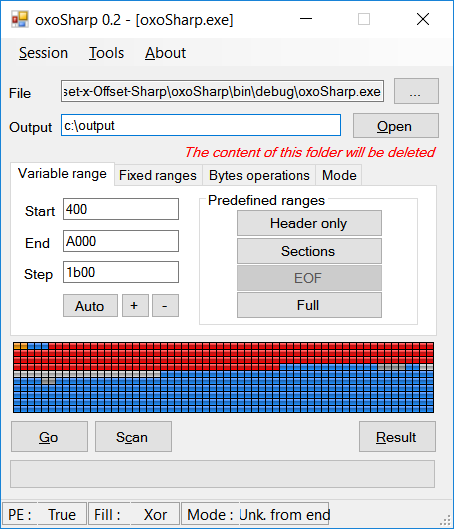
After selecting the "variable range" and the fixed ranges (optional) OXOSharp will create copies of the input file in the output folder, in each copy a range of bytes (from the variable range with the selected size) is replaced by dummy values (as configured). If the false viral signature is inside the selected "variable range", it's possible that at least one of the created file has it overwritten. This explains how the "Fixed size" mode works, it this fails because of the impossibility to find exactly the beginning and the end of range (a very big signature), the unknown size modes can be used
- Easy to use: Auto calculating step, selecting range from PE sections and the easy reintegration of previous result make the process easier
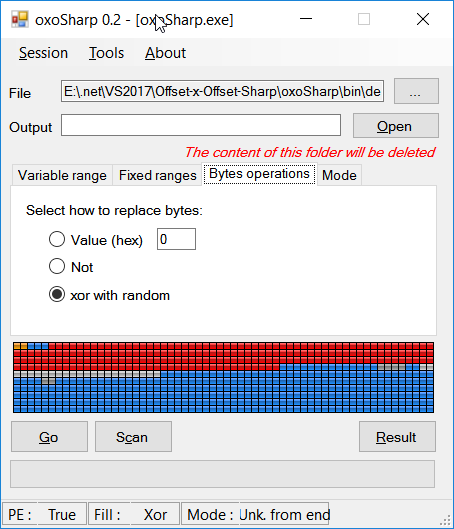
- Various bytes operation: can replace bytes by fixed value, by Boolean not or xor with a random value.
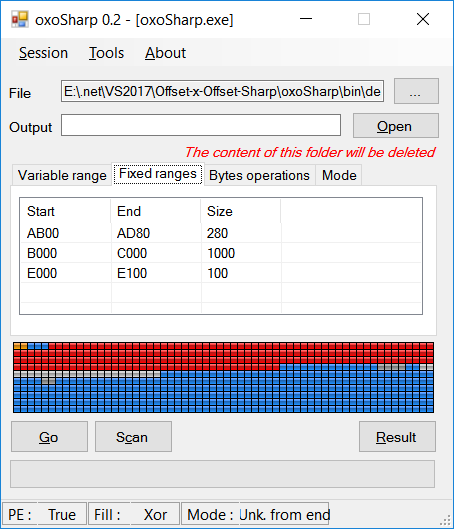
- Fixed ranges: in case of large signature which is a sign of multiple signatures, a fixed range can be added, this range will have bytes replaced in every created file.
- Different modes:
- Fixed size range: the range (that get bytes replaced) for every created file is adjacent to the previous and have the same size.
- Unknown size from start/end: the range for every created file has the same end (resp. start) offset, and moving start (resp. end) offset, and the range is included in the previous and smaller.
- Auto/Manual save session: the current session (ranges) is saved and load automatically when close/open the program, you can also save them manually
- Scan button: you can configure the program for the location of a console antivirus and its command line
Drop a file in the "File" textbox In variable range input a range (or leave the default)
(Optional) You can select a fixed range from sections (in first tab) or enter it manually (in the second tab), if you don't know what to put don't use it
In byte operations select how the bytes should be replaced (personally I use only "xor with random", the other modes are added for other users’ preferences)
Select the mode (explained above, or you can press the "?" button to see how it works)
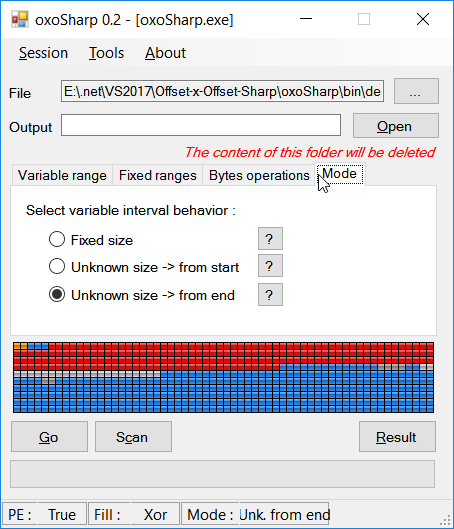
Press Go, the progress bar will fill, ones done scan the output folder, repeat selecting variable/fixed range(s) until you get the smallest undetected range which represent the viral signature.
Depending on the nature of the signature, data or code (in which sections it's found), is the program native or .net:
- Native:
- Code: you can move the code to a code cave or replace it with an equivalent one i.e different/obfuscated/encrypted instruction that do the same function.
- Data: I not used by the program (some stuff added by the compiler) fill it with blank, if used try to encrypt/decrypt them or inline them (depends of the size)
- .Net:
- Metadata: it's possible that the name of methods/classes cause detections, rename them
- Code: try obfuscating the detected method
Maybe the detection is not signature base but heuristic (based on behavior), and the work of OXOSharp just broke the program (so its execution inside AV loader didn't yield any suspect behavior). This program doesn't work for this case
The purpose of this program is to get rid of the false AV detections, you're the only responsible of what you do