Part of HTTP Toolkit: powerful tools for building, testing & debugging HTTP(S)
A tiny demo app using SSL pinning to block HTTPS MitM interception.
You can either clone this repo and build it yourself in Android Studio, or download the APK from the releases page and install it with adb install android-ssl-pinning-demo.apk.
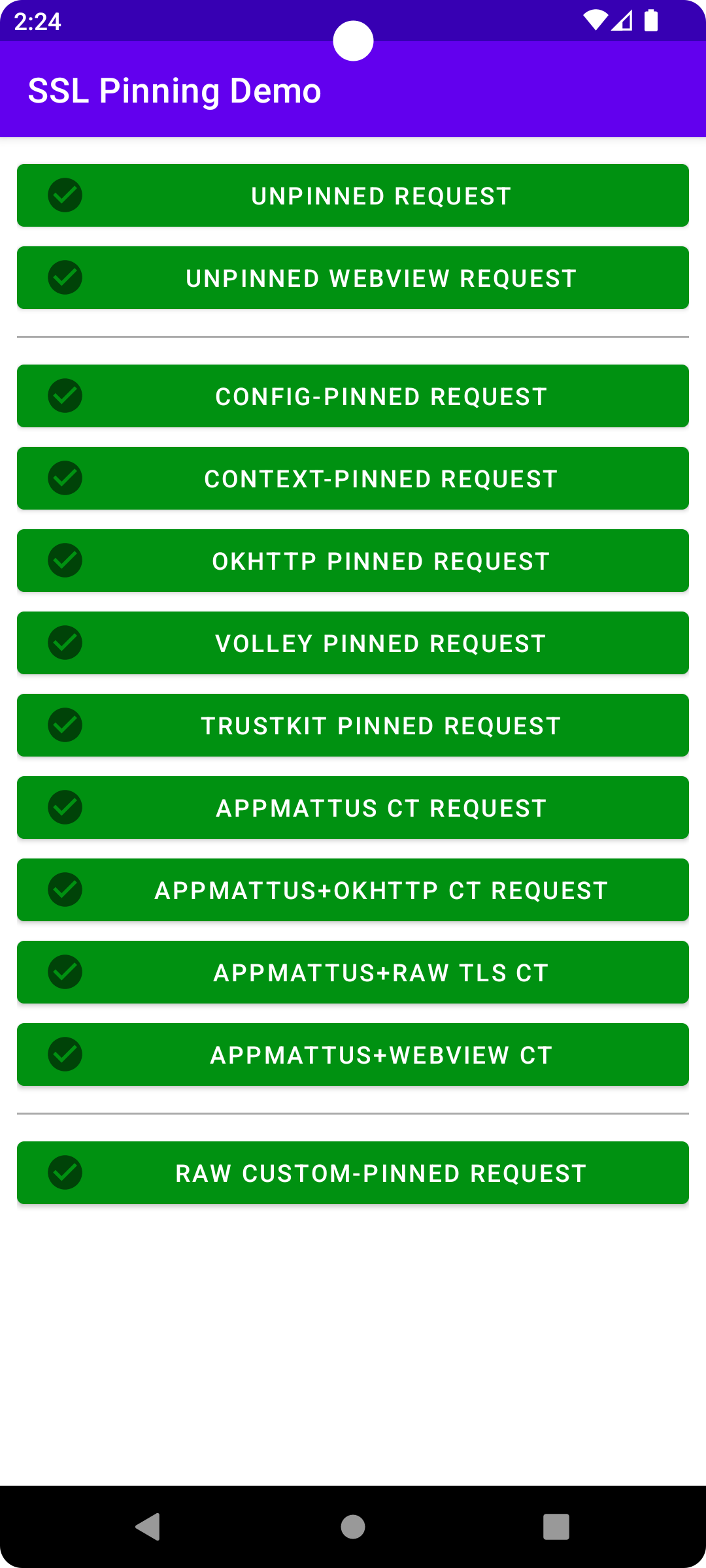
Pressing each button will send an HTTP request with the corresponding configuration. The buttons are purple initially or while a request is in flight, and then turn green or red (with corresponding icons and an error message popped up for failures) when the request succeeds/fails.
On a normal unintercepted device, every button should always immediately pass.
On a device whose HTTPS is being intercepted (e.g. with HTTP Toolkit), the unpinned buttons will pass, and then all other buttons the first 'unpinned' buttons will fail.
On an intercepted device using a standard Frida script (or similar) to automatically disable certificate pinning (e.g. https://github.com/httptoolkit/frida-interception-and-unpinning/) all buttons should pass except the final "custom-pinned" button.
That final button uses low-level manual checks against the TLS connection, with no external libraries or config involved. It is still possible to make this pass too, but you'll need to do a little reverse engineering to disable that code specifically. See this Android reverse engineering blog post for more details.