- Introduction
- Tools Used
- Pipeline
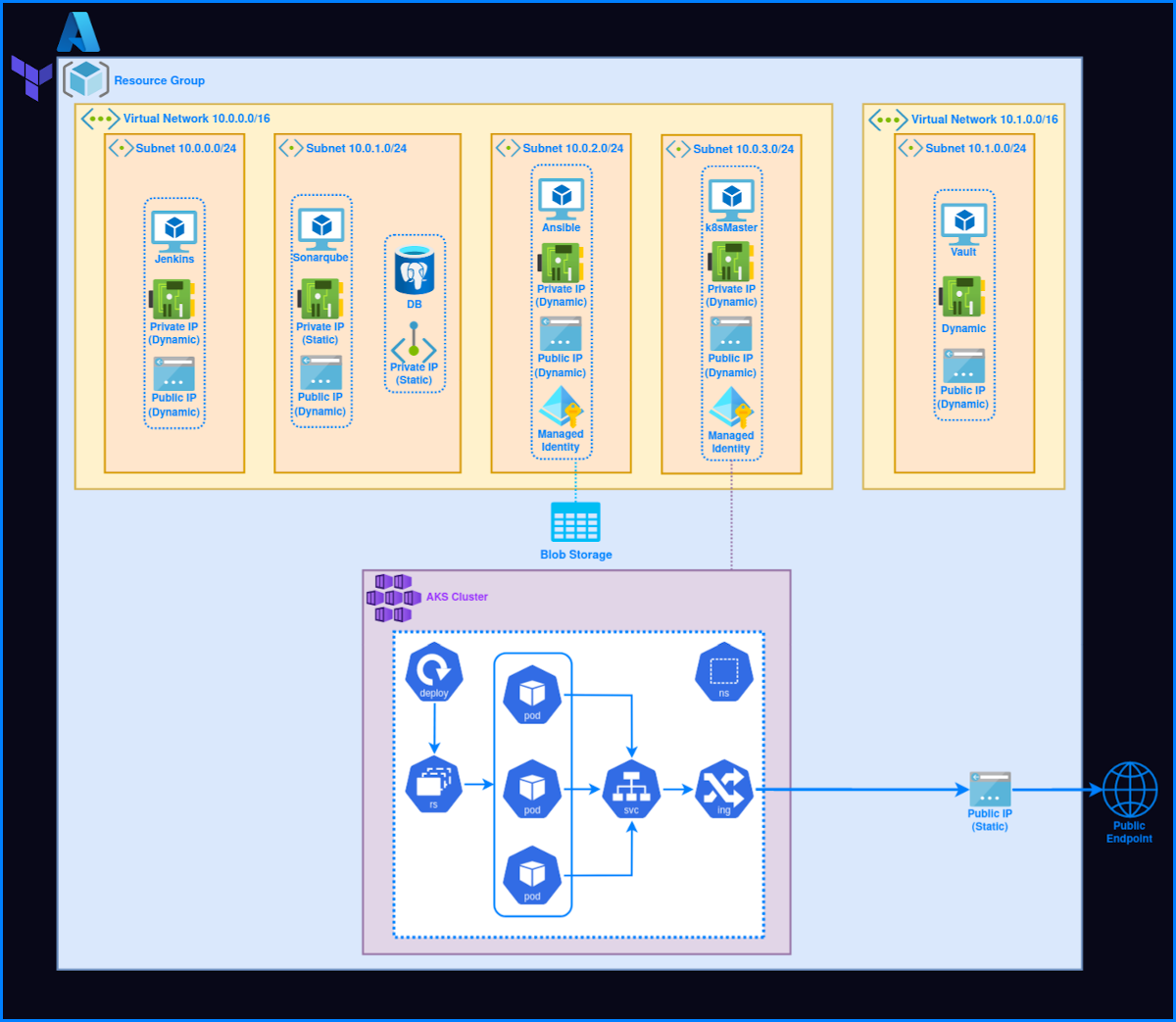
- Azure Infrastructure
- Detailed Workflow
- Security approaches
- Project Demo
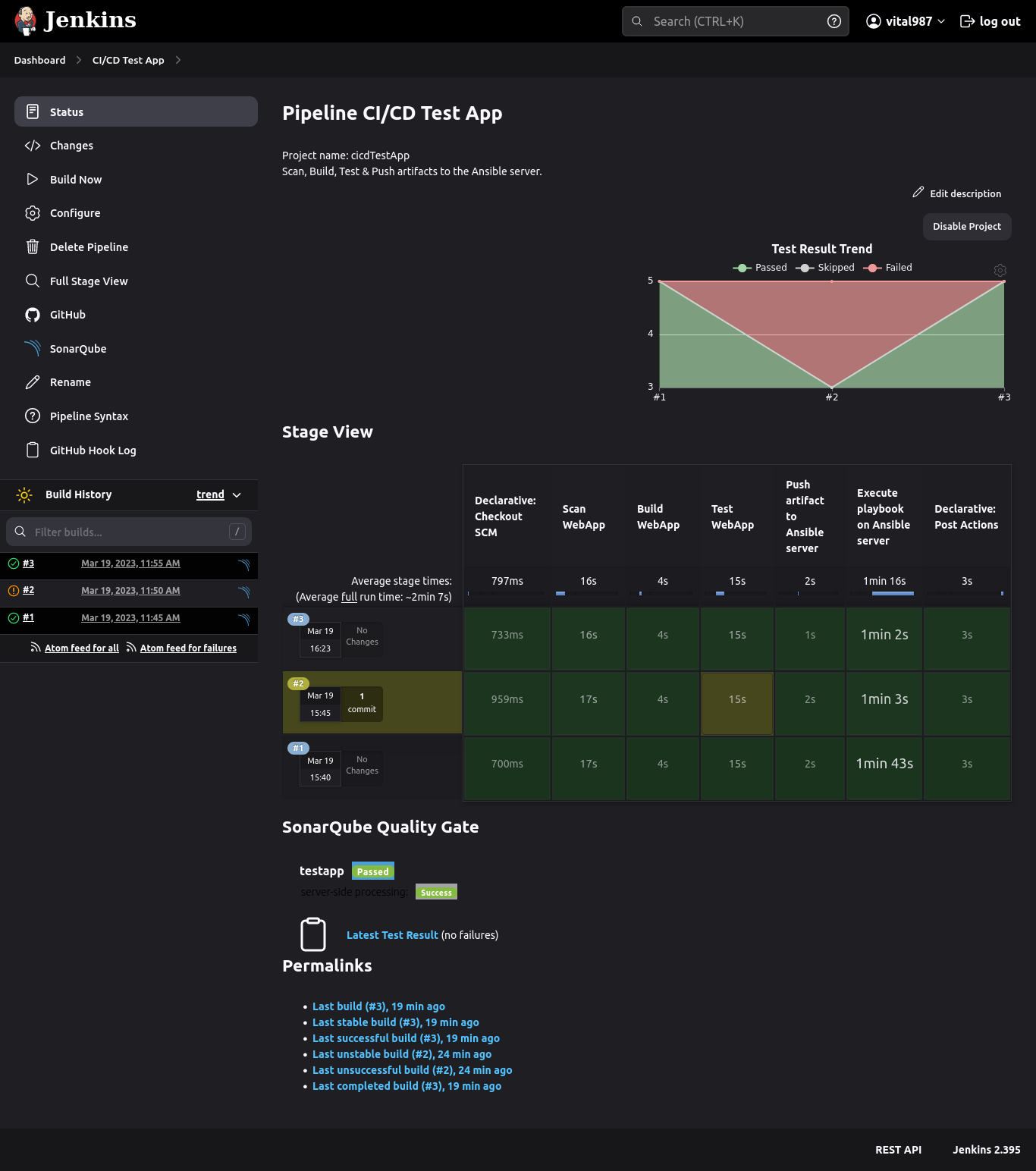
- Screenshots
- Build Outputs
An end-to-end DevSecOps pipeline built on Azure using Terraform.
Azure |
Terraform |
Linux |
|---|---|---|
Git |
GitHub |
Jenkins |
Vault |
Trivy |
SonarQube |
Maven |
JUnit |
Selenium |
Ansible |
Docker |
Kubernetes |
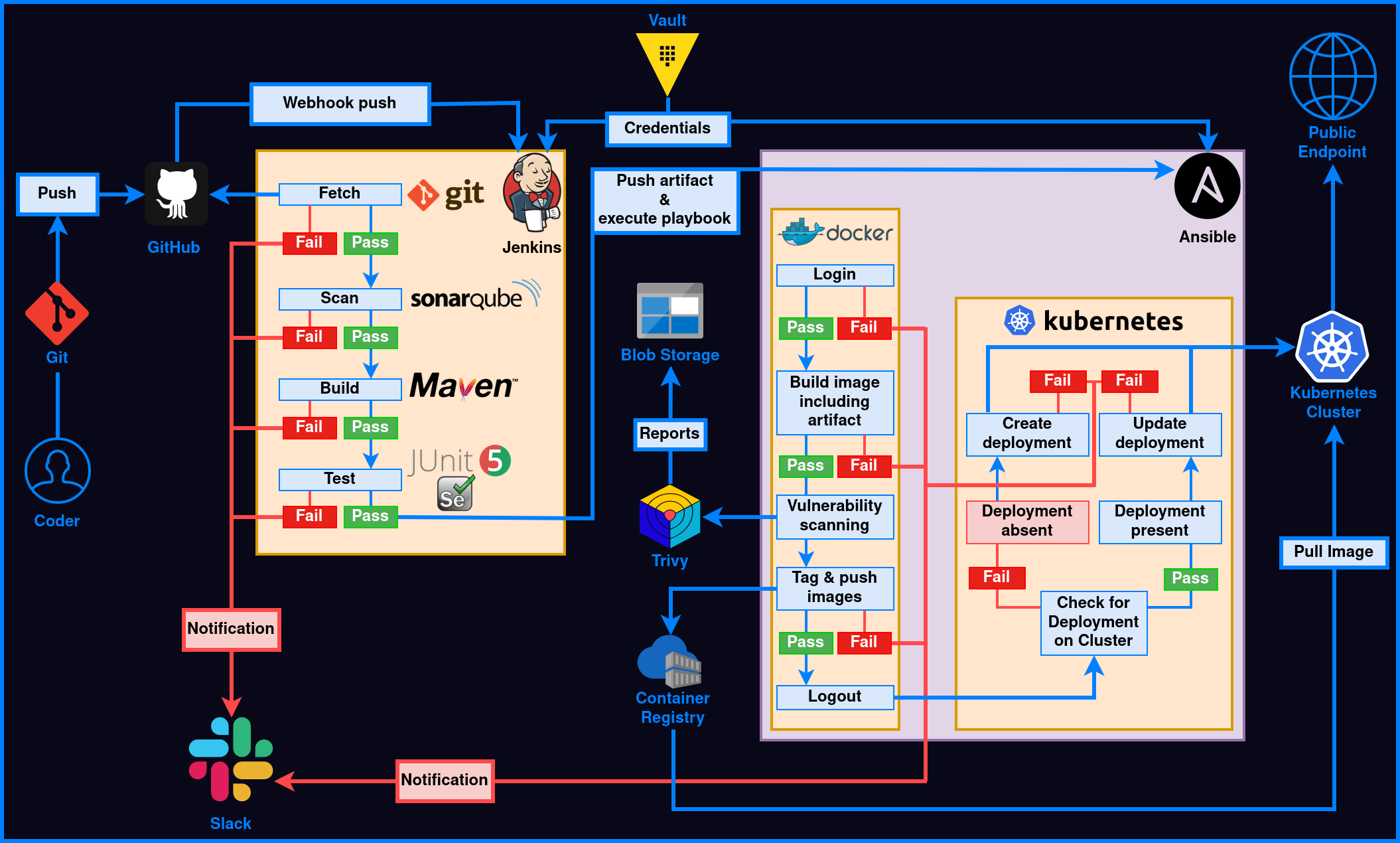
- The coder commits and pushes the source code to the GitHub repository.
- GitHub webhook pushes to Jenkins.
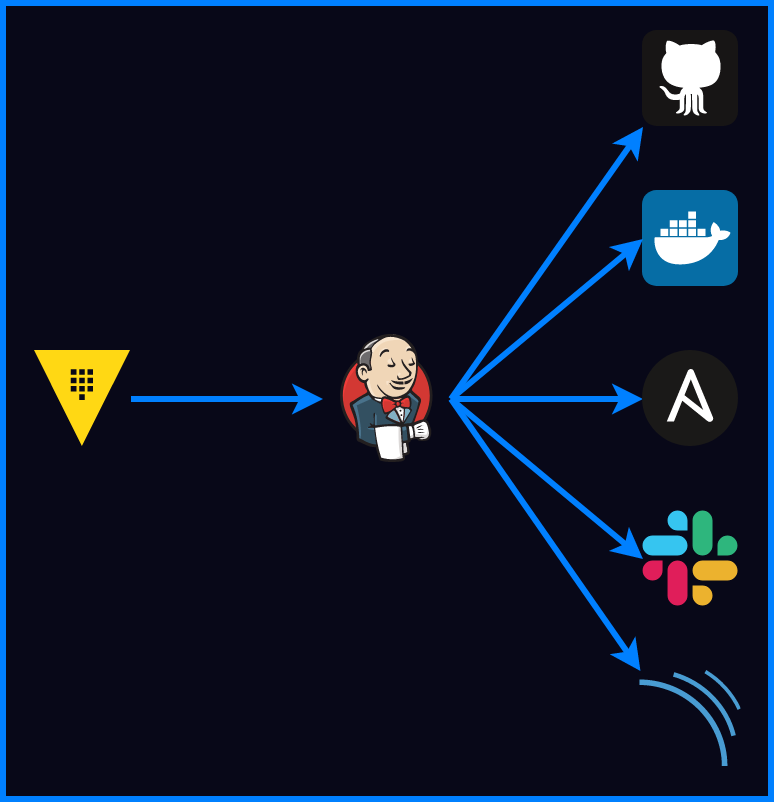
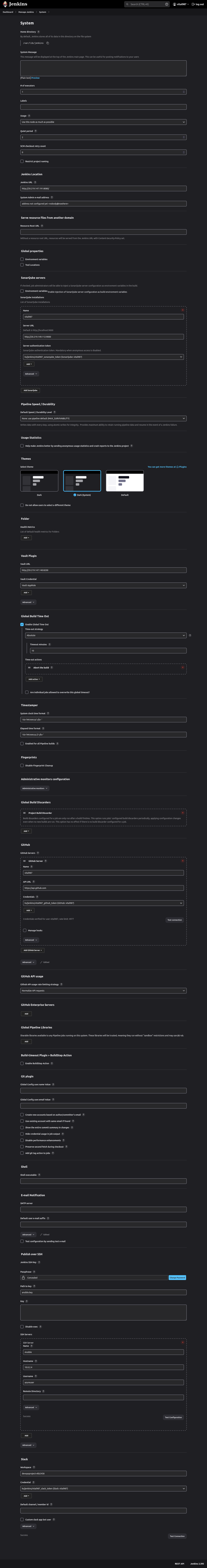
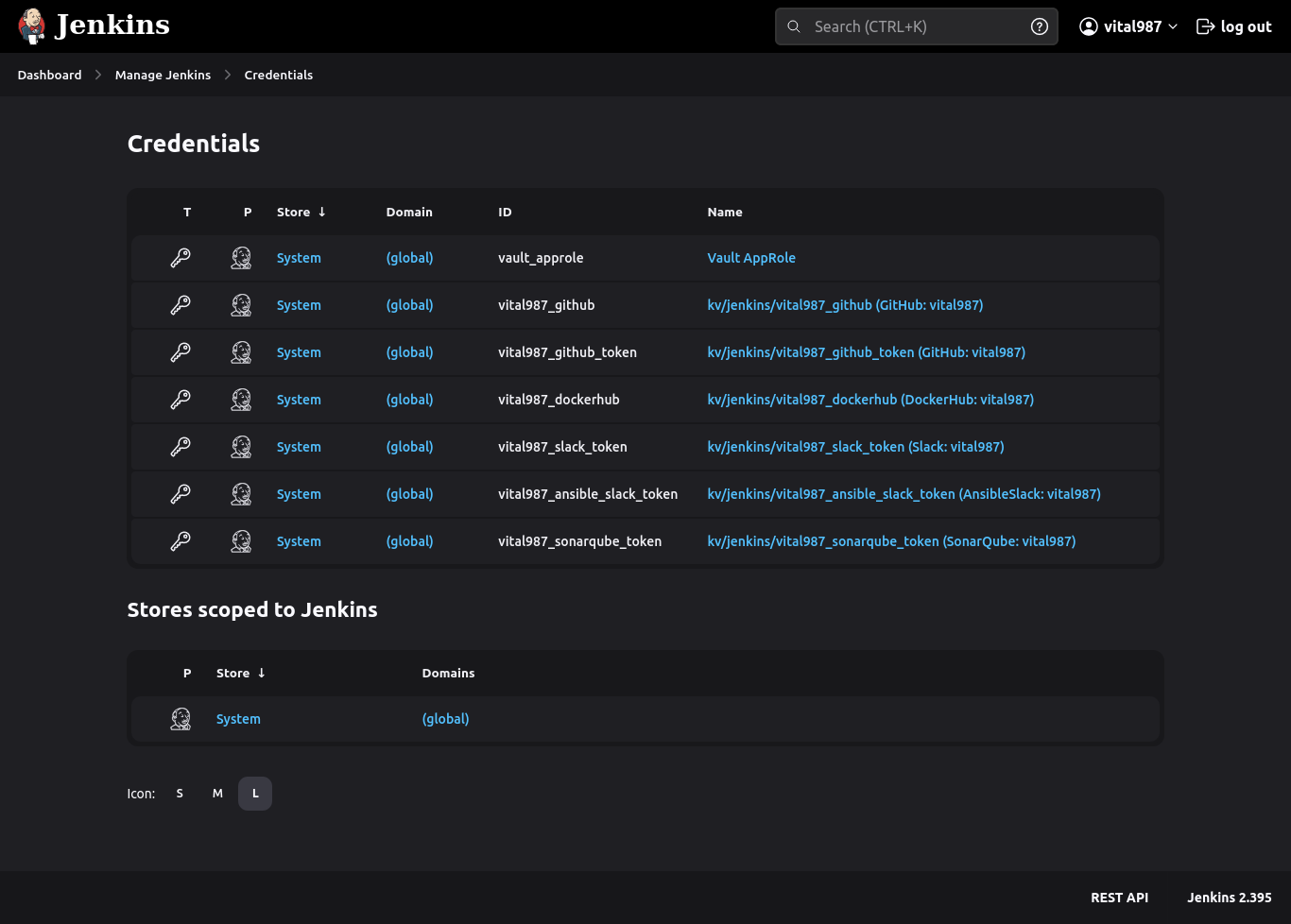
- Vault integration with Jenkins enables Jenkins to fetch credentials from Vault.
- Jenkins triggers the build.
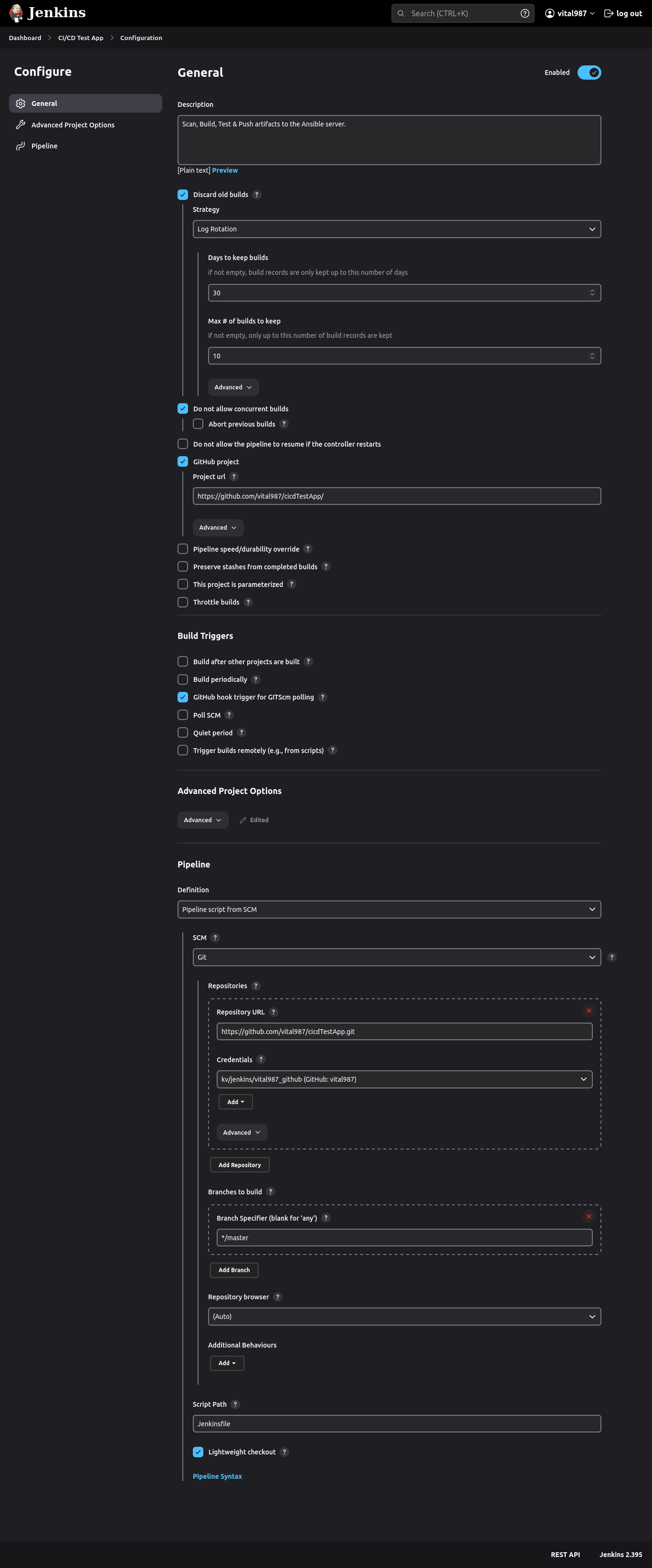
- Declarative Checkout: Jenkins fetches the source code from the GitHub repo and checks it out to the specified branch.
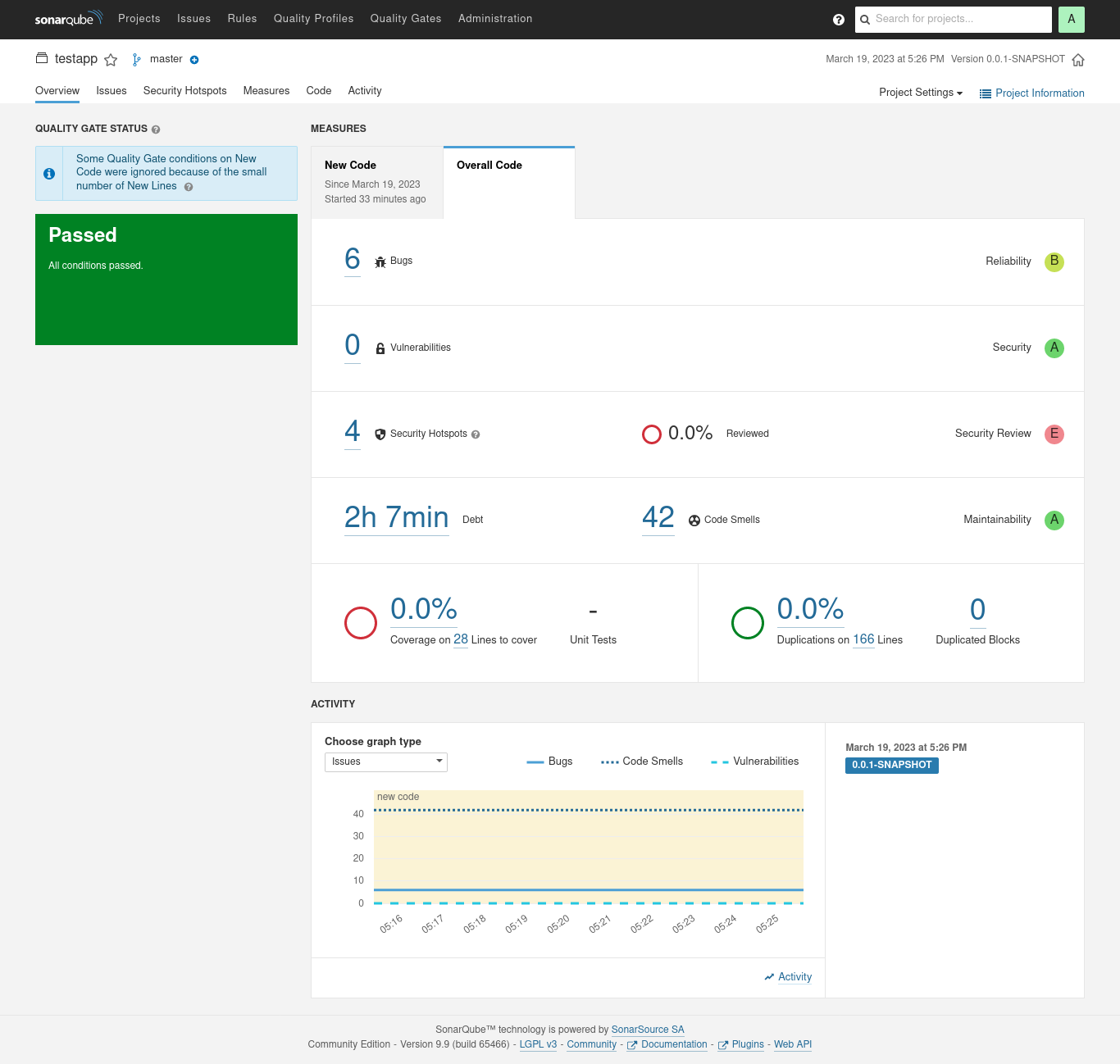
- Scan web app: Scans the fetched source code with SonarQube scanner and reports the analysis to the SonarQube host.
- Build web app: Builds the source code with Maven and outputs a jar file (war+tomcat server).
- Test web app: Tests the built application with given JUnit test cases and stores the reports with the help of the SureFire plugin.
- Push artifact: Pushes the built jar file to the Ansible server via SCP.
- Run the playbook: Run the Ansible playbook on the Ansible server.
- Clean workspace: Delete compiled/built/packaged components.
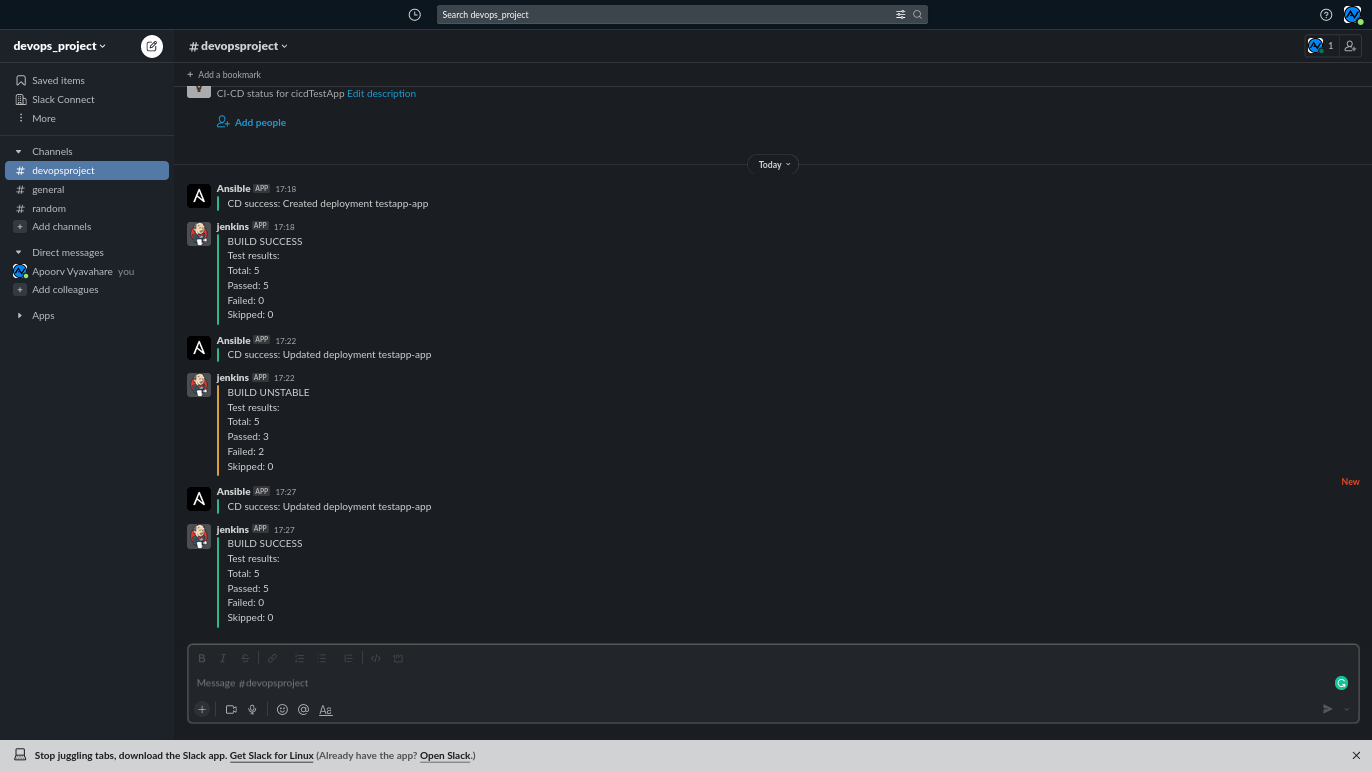
- Send status: Sends build status to GitHub and build status + test summary to Slack (the failure in any stage will also send notification).
- Ansible executes the playbook on the Ansible server.
- Docker login: Login to Docker with registry credentials (DockerHub in this case) to push images.
- Build image: Build the image by copying the JAR file (the artifact sent by Jenkins) into the image.
- Tag & push tagged image: Tag the built image with the current Jenkins build number and push to the registry (for update deployments).
- Tag & push latest image: Re-tag the above image with the "latest" tag and push it to DockerHub (for initial deployments).
- Docker logout: Log out of the DockerHub registry.
- Trivy vulnerability scan: Scan Docker images for vulnerabilities and secrets and upload reports to blob storage.
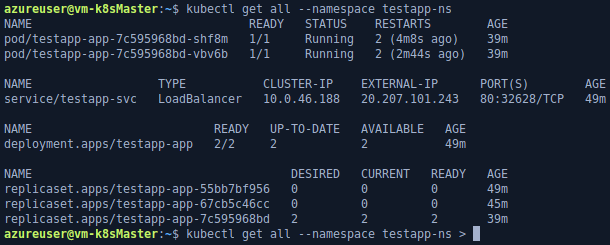
- Deployment check: check for the existence of deployment on a Kubernetes cluster via the master node.
- Create the deployment with the latest image if it doesn't exist.
- Update the existing deployment with the tagged image if it exists.
- Notify the deployment status to Slack (failure at any stage will also notify Slack).
- The deployment can be accessed publicly via a static public IP attached to the Nginx ingress controller of the cluster.
- One can further attach a domain name to the above IP.
- All the virtual machines are separated into their own subnets. The interconnection between subnets is blocked by NSG security rules.
- Other than the NSG rules mentioned above, each VM has its own NSG inbound rules, allowing only the ports used by the respective softwares.
- All the virtual machines are secured with SSH public key authentication, which will help prevent brute-force attacks. The ssh connections between required virtual machines are made using Terraform during infrastructure provisioning. The keys are optionally stored locally to access the virtual machines manually.
- The credentials of all the tools are stored securely in the Hashicorp Vault. The credentials are accessed only by Jenkins and distributed to the rest of the tools via pipeline interpolation, reason was to secure the Vault AppRole credentials. Cause, according to my perspective, Jenkins provides the most secure credential storage among all the other tools (except vault) used in the pipeline to store Vault access (AppRole) credentials.
Demonstration of the pipeline workflow. Click the above hyperlink to view the demo.
- Terraform
- Jenkins
- Vault